I just finished reading Neal Stephenson's Novel
Cryptonomicon. In the book, two characters in prison use a deck of cards to encrypt their written communications. Well, it turns out that it's actually a real encryption technique invented by Cryptologist Bruce Schneier for the book, but it is also intended to provide serious security in actual field use, check it out, it's a pretty cool concept. Here is the overview from Scneier's Website:
http://www.schneier.com/solitaire.html
"In Neal Stephenson's novel Cryptonomicon, the character Enoch Root describes a cryptosystem code-named "Pontifex" to another character named Randy Waterhouse, and later reveals that the steps of the algorithm are intended to be carried out using a deck of playing cards. These two characters go on to exchange several encrypted messages using this system. The system is called "Solitaire" (in the novel, "Pontifex" is a code name intended to temporarily conceal the fact that it employs a deck of cards) and I designed it to allow field agents to communicate securely without having to rely on electronics or having to carry incriminating tools. An agent might be in a situation where he just does not have access to a computer, or may be prosecuted if he has tools for secret communication. But a deck of cards...what harm is that?
Solitaire gets its security from the inherent randomness in a shuffled deck of cards. By manipulating this deck, a communicant can create a string of "random" letters that he then combines with his message. Of course Solitaire can be simulated on a computer, but it is designed to be implemented by hand.
Solitaire may be low-tech, but its security is intended to be high-tech. I designed Solitaire to be secure even against the most well-funded military adversaries with the biggest computers and the smartest cryptanalysts. Of course, there is no guarantee that someone won't find a clever attack against Solitaire (watch this space for updates), but the algorithm is certainly better than any other pencil-and-paper cipher I've ever seen.
It's not fast, though. It can take an evening to encrypt or decrypt a reasonably long message. In David Kahn's book Kahn on Codes, he describes a real pencil-and-paper cipher used by a Soviet spy. Both the Soviet algorithm and Solitaire take about the same amount of time to encrypt a message: most of an evening"















 If your bathroom needs that little bit of lockup luxury, the Neo Metro combi might be just the thing your looking for. Or if you prefer the real deal, Bradley Plumbing makes basically the same item, but industrial strength. What makes a toilet industrial strength? Well the seat of the Bradley toilet sink combo can withstand a weight of 5,000 pounds. If you prefer a locker room vibe, Bradley also makes those multi head column showers and the always popular 5 person handwashing basin - same one we all used in elementary school, half round, foot operated. if you need a reminder, this is what I am talking about -->
If your bathroom needs that little bit of lockup luxury, the Neo Metro combi might be just the thing your looking for. Or if you prefer the real deal, Bradley Plumbing makes basically the same item, but industrial strength. What makes a toilet industrial strength? Well the seat of the Bradley toilet sink combo can withstand a weight of 5,000 pounds. If you prefer a locker room vibe, Bradley also makes those multi head column showers and the always popular 5 person handwashing basin - same one we all used in elementary school, half round, foot operated. if you need a reminder, this is what I am talking about -->


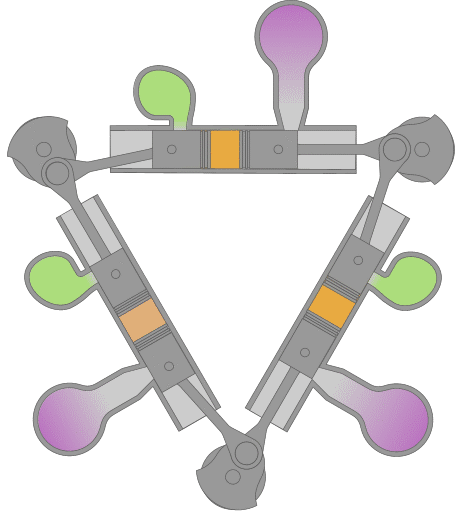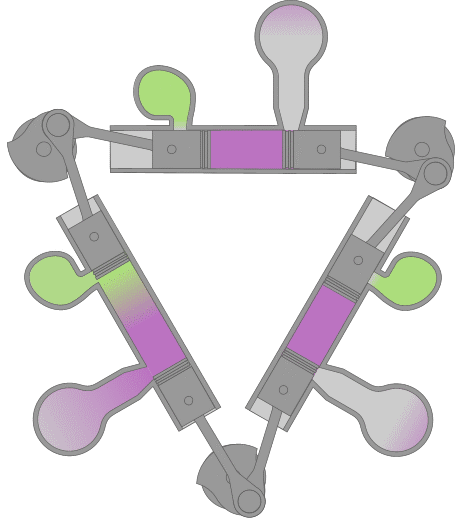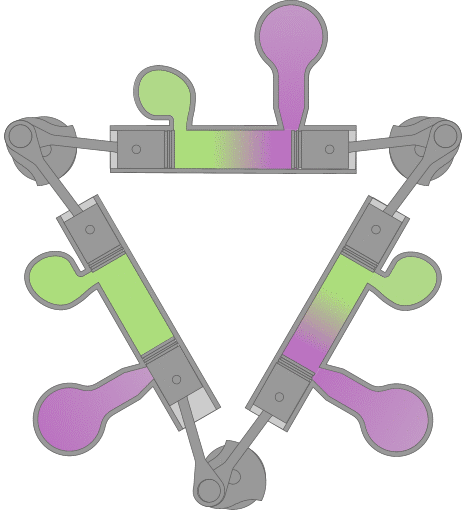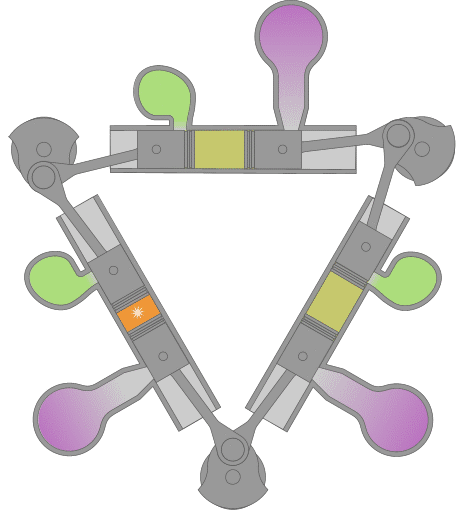 Designed and produced by the British company D. Napier and Sons in the years following WWII. It was designed to replace the gasoline engines then used in PT Boats. Compact & lightwieght, (1/5 of a contemporary diesel) the Deltic was an ideal design for high speed marine use and had considerable success in that application. Napier Deltics also saw some limited use as a locomotive engine. Because of it's compact dimensions and subsequently low magnetic signature, it is still being used to power British minesweepers.
Designed and produced by the British company D. Napier and Sons in the years following WWII. It was designed to replace the gasoline engines then used in PT Boats. Compact & lightwieght, (1/5 of a contemporary diesel) the Deltic was an ideal design for high speed marine use and had considerable success in that application. Napier Deltics also saw some limited use as a locomotive engine. Because of it's compact dimensions and subsequently low magnetic signature, it is still being used to power British minesweepers.






